Two-factor authentication is probably the best way to protect against remote attacks nowadays. You may take numerous precaution measures to protect your computer, but you can never be 100% sure your credentials are not compromised.
Sophos UTM provides built-in support of two-factor authentication. And as with all other features in UTM, 2FA feature is implemented in a very user-friendly interfaces.
In my previous blog post I showed how easy to enable and configure different types of Remote Access with Sophos UTM. Today we will see how to secure the Remote Access with OTP.
Additionally, we will review the installation of third-party SSL certificate from one of the providers that is trusted by your browser. Not that I expect some phishing attacks on my home lab, but it will stop the browser throwing the certificate error every time you access UTM User Portal.
Ok, let's start with OTP configuration.
1. Log into Sophos UTM and go to Definition & Users - Authentication Services
2. Open One-Time Passwords tab and enable the service
- Check that 'Auto-create OTP tokens for users' setting is enabled
- Check that OTP is enabled for User Portal
- Check that OTP is enabled for SSL VPN Remote Access
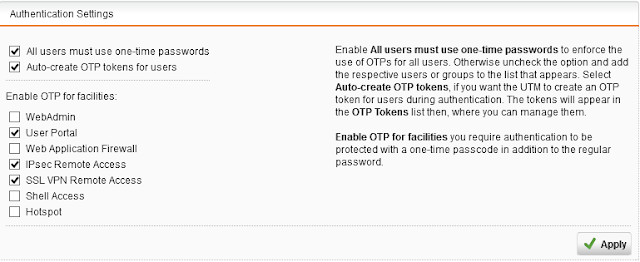
3. That's it. See how simple it is?
Now let’s have a look at how we get it working.
1. Install Google Authenticator app on your mobile.
2. Login to the user portal with your credentials. Note, you can't use OTP yet.
3. You will immediately see the QR code which you will need to scan with Google Authenticator
4. Once Google Authenticator successfully reads the QR code press Proceed with login button which will bring you to the login page again
5. In the password field you have to type your password directly followed by passcode displayed by Google Authenticator.
6. Now you can see the details of your OTP in the User Portal
Use the same combination of Password+Passcode when you authenticate with SSL VPN client
One last thing. In case you loose your phone or you brake it, or the phone is reset and Google Authenticator is not there anymore you won't be able to authenticate to Sophos UTM.
One last thing. In case you loose your phone or you brake it, or the phone is reset and Google Authenticator is not there anymore you won't be able to authenticate to Sophos UTM.
For this type of situations you might wanna have some pre-generated authentication codes stored somewhere in a safe and secured place. To get these codes:
- Go to One Time Password tab again.
- Click the Edit button on your username entry
- Expand the Advanced Settings and press the green Plus button to generate one time passwords.
Now let's talk about 3rd party certificate installation.
You will need your own domain name. When you request a certificate the Certificate Authority will normally require you to validate the domain name ownership by sending verification code to the email address of the domain owner or by asking you to create a DNS records for that domain.
1. Generate a pair of keys
openssl genrsa -aes256 -out myUTM.key 2048
2. Generate Certificate Signing Request
openssl req -new -key myUTM.key -out myUTM.csr
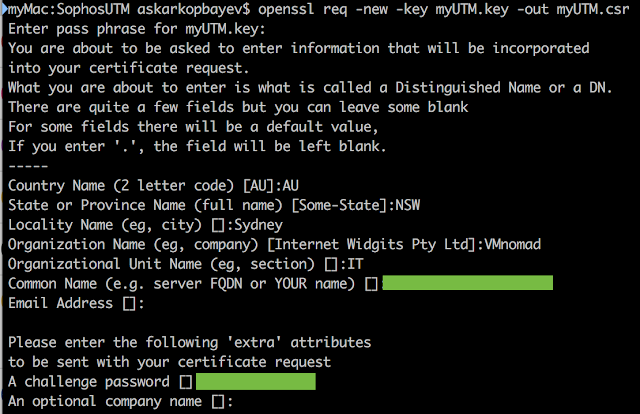
3. Upload CSR to a third party Certificate Authority
4. Download the signed certificate from the CA
5. Using the certificate from the CA and the key file generate PKCS12 file.
openssl pkcs12 -export -in Cert.pem -inkey myUTM.key -out myUTM.p12
Please note that you have to use .pem format. Don't use .p7b or .cer format of the certificate, otherwise you will get the following error6. Upload the PKCS12 certificate to the Sophos UTM
7. And finally configure UTM to use the new certificate for Web pages
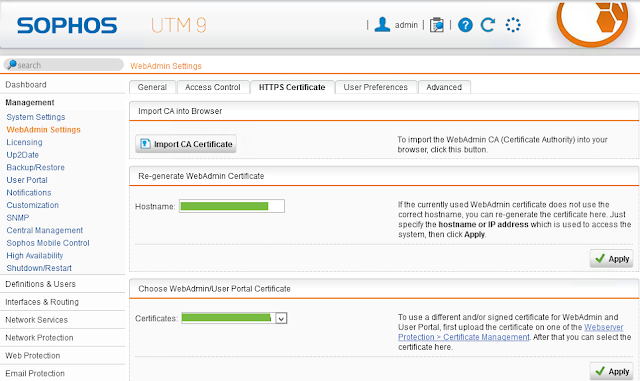
As you see Sophos UTM again proves to be an ideal virtual networking solution for a home lab.







No comments:
Post a Comment